Monthly Archives: February 2010
User state migration fails on a SCCM 2007 SP1 or SP2 client after you install security update 974571 – SCCM Hotfix available: KB977203
The actually workaround before this hotfix came out, was is to uninstall the 974571 hotfix on computers before running USMT task sequence. This workaround works fine but was not sufficient for many customers (The opposite would have been funny ).
Consider the following scenario:
- You install the System Center Configuration Manager 2007 Service Pack 1 (SP1) client or the System Center Configuration Manager 2007 Service Pack 2 (SP2) client.
- You install security update 974571 on this computer.
- A SCCM task sequence runs on this client. This task sequence includes the Capture User State task sequence step and the Restore User State task sequence step.
In this scenario, user state migration fails. At the same time, the following error message is logged in the Ccmexec.log file:
Failed to import the client certificate store (0x80092024) OSDSMPClient
For all the details including a download link to the hotfix see the following new Knowledge Base article:
KB977203 – User state migration fails on a SCCM 2007 SP1 client or on a SCCM 2007 SP2 client after you install security update 974571
Microsoft System Center Configuration Manager 2007 SP2 Evaluation
Brief Description
Overview
- New Operating System Support
- Windows 7
- Windows Vista Sp2
- Windows Server 2008 R2
- Windows Server 2008 SP2
- New Features in Out of Band Management
In addition to providing feature parity with SP1 and AMT firmware versions 3.2.1, 4.0 and 5.0, the following new features are supported:- Wireless management with up to 8 wireless profiles
- End point access control: 802.1x support
- Audit logging
- Support for different power states
- Power control options at the collection level
- Data storage
- Scheduling configuration for in-band provisioning
- Asset Intelligence Certificate Requirement Removal
Configuration Manager Service Pack 1 introduced Asset Intelligence v1.5. This version allowed customers to configure an online synchronization to ensure that their catalog was up to date with the latest Microsoft inventory for both hardware and applications. This initial release required a certificate. With Service Pack 2, the requirement to have the certificate has been removed, so any customer can configure their Asset Intelligence capabilities to connect online and update their catalog. Software Assurance is not required for this functionality. - 64-bit Architecture Development
Service Pack 2 will also continue to deliver new support for x64 architectures, including the following:- X64 support for Operations Manager 2007 Client Agent
- Update to Management Packs for 64-bit operating systems – SP2 will ship 64-bit performance counters (the management pack is a separate release)
- Remote control support added for x64 XP and x64 Server 2003
- Improved Client Policy Evaluation
- Faster policy processing
- More efficient software distribution configured to run at user logon
- Branch Cache Support
Support for scenarios where Windows Server 2008 R2 and Windows 7 Client are present and Branch Cache is enabled
System Requirements
- Supported Operating Systems: Windows 2000 Advanced Server; Windows 2000 Service Pack 4; Windows 7; Windows Embedded for Point of Service ; Windows Server 2003; Windows Server 2003 R2 (32-Bit x86); Windows Server 2003 R2 Enterprise Edition (32-Bit x86); Windows Server 2003 Service Pack 1; Windows Server 2003 Service Pack 2; Windows Server 2008 Datacenter; Windows Server 2008 Enterprise; Windows Server 2008 R2; Windows Server 2008 Service Pack 2; Windows Vista Ultimate
10 Ways to Secure Windows 7
Use the Windows 7 Firewall
The firewall in Windows 7 is a spin off of Windows Vista and is easy and is very secure and powerful. With features to secure you and step by step instructions, Windows 7’s firewall is a very powerful firewall that allows a detailed configuration giving the end user true protection from malicious threats.
Backup Your Data
Windows 7 allows you an easier to use backup option that allows you to walk through a step by step backup of your critical data. This option is often over looked by home users. The simple and easy to use backup allows the end user to backup their data in the event of a system crash. Microsoft Windows 7 allows for a system image to be created as well as files to be backed up.
Use Internet Explorer 8
A recent study showed Internet Explorer 8 beat out Firefox and other major browsers in protecting your computer. With SmartScreen Filter, this addition allows users to surf websites that are labeled in Microsoft’s database as legitimate or malicious. Go to the Safety menu for more information on how to enable this option. Cross-site scripting and other websites that are vulnerable are noted.
Enable BitLocker
This encryption can allow the entire volume of your computer to be secured. With BitLocker, you can encrypt the boot system and any removable media on your computer. With USB thumbdrives being portable, this is one of many ways you can encrypt your system. Third party software such as Truecrypt, blah and blah which are all Windows 7 compatiable, Windows 7 can be further encrypted to provide a strong barrier against data theft. Always save your encrypted information and passwords / phrases. Loss of these items can result in you losing your valuable information.
Updates and Patches
Microsoft years ago set aside security dates monthly to ensure computers had hotfixes / patches to ensure your computer is protected. Although these patches are for Windows, you should look at SUMo or Secunia to ensure your computer’s applications are also patched.
Antivirus / Antimalware
Ensuring your computer has protection against viruses and malware is essential. With the dozen or so applications that are free to use, these applications provide protection against the malicious injection of viruses or malware on your system. With zero day threats along with malicious activities found on thousands of websites, antivirus and antimalware protection allows further protection against these threats from infecting your computer.
Keep the UAC
Keeping the ‘what users call’ annoying UAC prompts helps you make the critical descisions in and when installing software. With smarter malware and viruses, the UAC helps you decide on what is legitimate and what may be a dangerous piece of software. Windows 7 allows you to adjust this protection agent. The UAC in Windows 7 is less annoying than Windows Vista. Microsoft has adjusted this feature to help the end user.
Sharing Information
When sharing out files or folders, make sure you only allow specified users to assess your data. With Windows 7 Folder and File sharing being easier than ever, you must specifiy individual users whom you wish to share the data. Never allow all users to veiw data and avoid appications such as P2P file sharing programs to share out information on your hard drive. Research has shown that using such software leaves users vulnerable to accidently placing files in the shared folder and users across the globe have access to the data in the shared folder.
Restricting User Access
Physical security plays an important role in computer security. Many homes and business allow the sharing of a common computer. Setup individual accounts to ensure users are logging in and creating their own sessions. Assign a user role to the computer user. Do not allow everyone to be an administrator of a common computer. This can result in many logistical nightmares from the addition of users you are unaware of, removal or addition of software and many other security nightmares. Always lock your computer when away from it for any period of time. You can do this by holding down the Windows key and hitting the ‘L’ key to lock it.
Using Email and the Internet Wisely
Many articles have been written warning users not to click fishy and unknown ads on the web, opening unknown email or going to websites that are malicious in nature. All of the information stated in these articles are true. Don’t open any email that you don’t know where it came from and don’t surf the web without surfing wisely. Restrict children from surfing the internet and control their surfing habits by using Windows 7’s Parental Controls with Web Filtering.
Conclusion
In conclusion, Windows 7 is secure out of the box. Using the above tips, the end user can further secure their system. By using antivirus, antimalware, UAC and other items, you can enhance the security of Windows 7 or any operating system.
Error creating MDT Boot Image
The error occurred after upgrading from SCCM SP1 to SCCM SP2.
I did a clean install of the SCCM with SP1 and after that i upgraded with SP2.
Seems to be related to the WAIK installtion that comes with SCCM SP1.
Remove the already install WAIK, Reinstall the latest WAIK.
That solved my problem.
the error shown in smsprov.log :
e:nts_sms_fresmssiteserversdk_providersmsprovsspbootimagepackage.cpp(2948) : Failed to read image property from the source WIM file due to error 80004005
Hypervisor not running
I’m running Windows Server 2008 R2 on my laptop and after I Hyper-V role the following error message showed, when trying to start a Hyper-V machine. Seems the Hyper-Visor entry was never made to the BCD store.

To add the hypervisor auto launch into the BCD store you’ll need to run the following command in administrator mode
bcdedit /set hypervisorlaunchtype auto
make sure virtualization feature is enabled in BIOS!
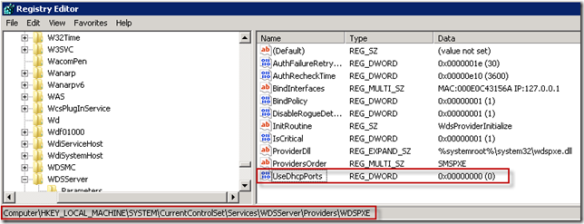
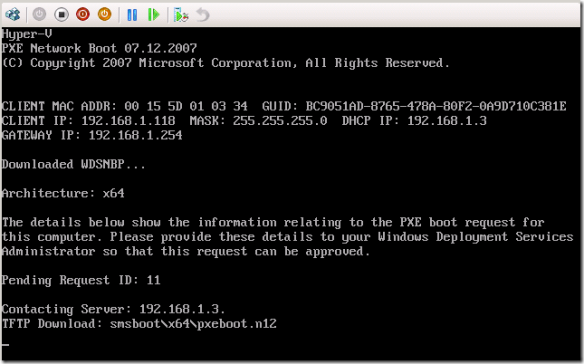
ConfigMgr OS Deployment – WDS and DHCP on same server Issue/Resolution
Recently I set up a Windows 2008 server with ConfigMgr 2007 SP1 (aka SCCM 2007) & wanted to do OS deployment. I ran into some issues because this server was also a DHCP server, this post will address the high level steps I took to get this working.
- Installed WDS via the Add Roles Wizard
- Added the PXE service point role via ConfigMgr Admin Console
- Now all should be good right? Nope, the WDS service would not start. After some research I found the issue to be that WDS & DHCP both use port 67 by default.
- I then removed and reinstalled the PXE service point and thought all was well – even the pxecontrol.log looked good (see below)
- Monitored PXEControl.log to ensure PXE was responding to tests
- So I tried to PXE boot a system and still no luck. More research showed that I needed to accomplish two more steps
- The next test worked like a charm